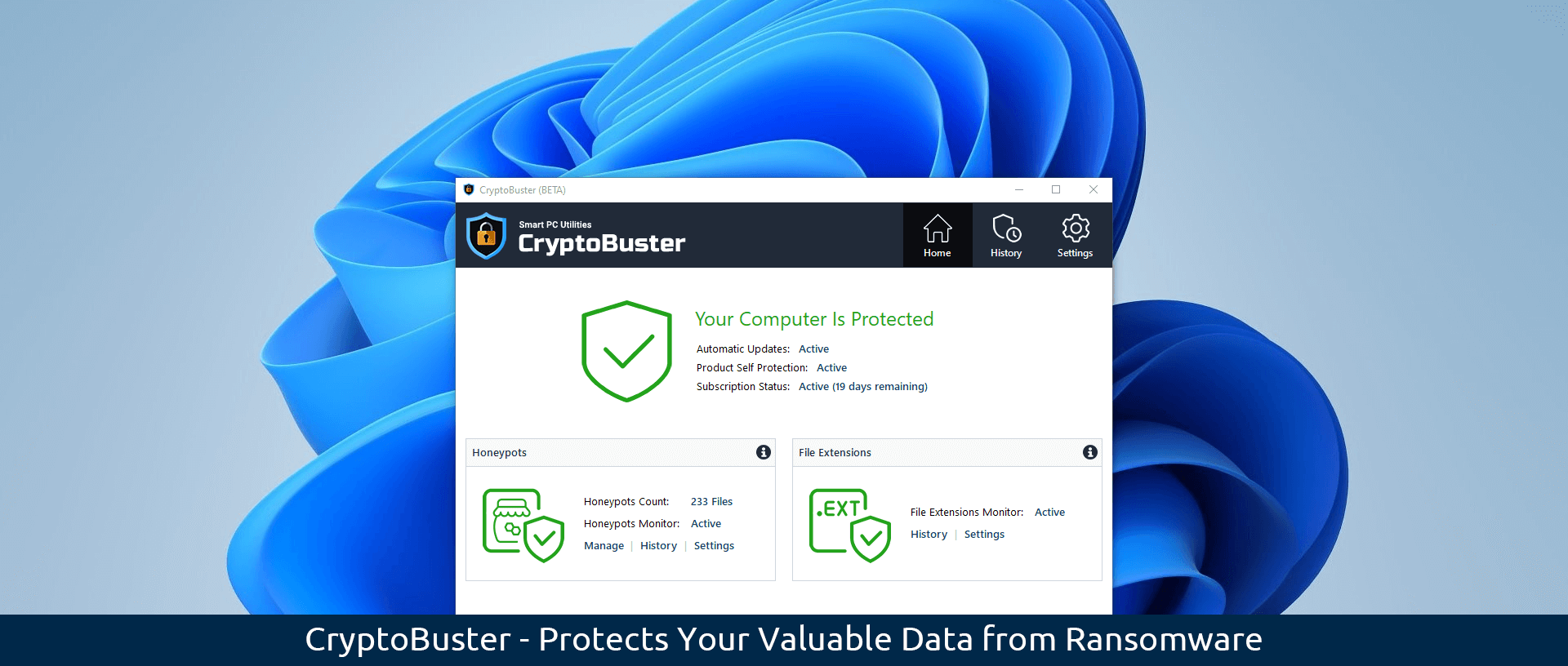
We at Smart PC Utilities are very excited to announce the release of the second beta of our anti-ransomware software CryptoBuster. This new update brings a small but important set of changes and bug fixes that aim to improve the software’s performance and reliability and, therefore, the user experience. You can download the
Continue readingAnti-Ransomware CryptoBuster v1.0.935 Beta 2 Released