We at Smart PC Utilities are proud to announce the release of the first Beta of our new anti-ransomware solution CryptoBuster. We designed our new software solution to work with your existing security product to offer an additional security layer and form the last line of defense against ransomware to protect your valuable data from permanent damage.
CryptoBuster features a user-friendly interface that makes it very easy to use and customize; it also has a small system footprint so that it can run side by side with your existing security solution without affecting the system’s performance.
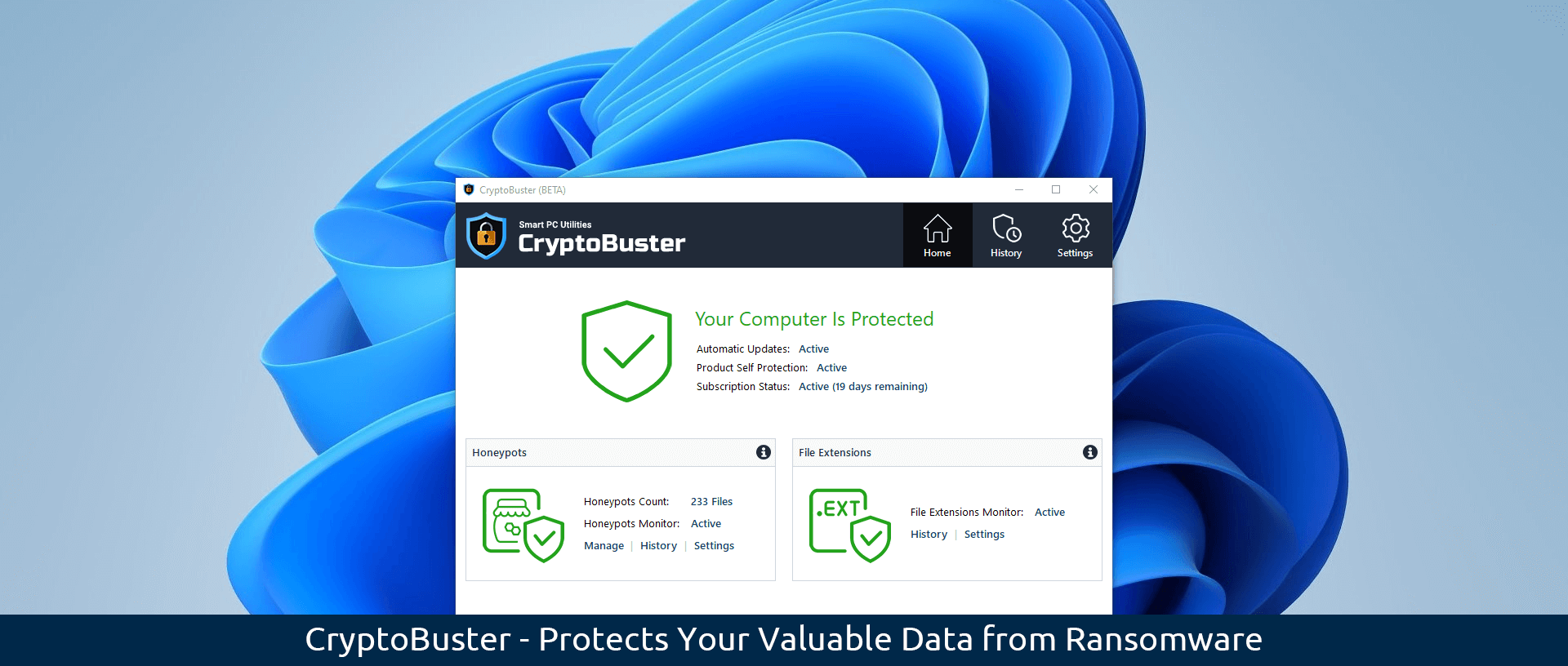
The current CryptoBuster Beta offers two main protection modules to help detect and stop ransomware, Honeypots and File Extensions Monitor.
Honeypots
Honeypots are decoy files that CryptoBuster uses to detect malicious activities on your computer; this is an efficient and proven technique with low false-positive chances of detecting and stopping ransomware when they start to encrypt the user files.
You can either create honeypots manually customizing their names, locations, and file types, or you can take advantage of the Honeypots Wizard which can deploy dozens of honeypot files in all critical system locations using custom names and file types that would allow ransomware to target those honeypots before they start to encrypt the user’s files, thus protecting important data from being encrypted by ransomware.
CrpyotBuster will instantly monitor the created honeypots and will notify you when an unauthorized program changes a honeypot file as this strongly indicates malicious activity. Besides notifying the user about honeypot changes, CryptoBuster can be configured to respond to honeypot changes with a series of actions aimed to prevent data damage like sending an email notification, suspending the program that changed the honeypot then terminating its process tree, and disabling all active network adapters.
Learn more about honeypots and how to use them to protect your computer from ransomware from the CryptoBuster user guide.
File Extensions Monitor
Besides Honeypots that are effective in stopping ransomware when they start to encrypt the user files, File Extensions Monitor can monitor the file system to detect the creation of specific types of files that may indicate ongoing ransomware attacks or sometimes may indicate the preparations for an attack.
For instance, CryptoBuster can detect the creation of files with extensions that are known to be used by ransomware to encrypt user files, also you can configure CryptoBuster to detect the creation of potentially dangerous files like batch files and scripts that are commonly used in ransomware attacks, or even to detect the creation of files of unknown types which is an aggressive technique used to stop most of the ransomware strains that change file extensions.
Learn about the File Extensions Monitor and how to properly configure it to help detect ransomware from the CryptoBuster user guide.
Roadmap
We will continue to improve the existing CryptoBuster protection modules and introduce new ones; here are some features and ideas we are working on:
- The development of a Windows Driver to intercept and block ransomware at the Kernel level.
- Support the creation of honeypots and file monitoring in network shares.
- A new protection module to monitor services, scheduled tasks, and startup programs to prevent ransomware from achieving persistence.
- Working on techniques to detect and prevent data exfiltration.
Please feel free to report any bugs and share any feedback and suggestions you have; this will greatly help us improve our software solution.
System Requirements
- Microsoft Windows 11 v10.0.22000 and later.
- Microsoft Windows 10 2004 and later (32-bit and 64-bit).
- Microsoft .NET Framework 4.8
Free 30-day CryptoBuster Trial
Leave a Reply Cancel reply