CryptoBuster Settings
General
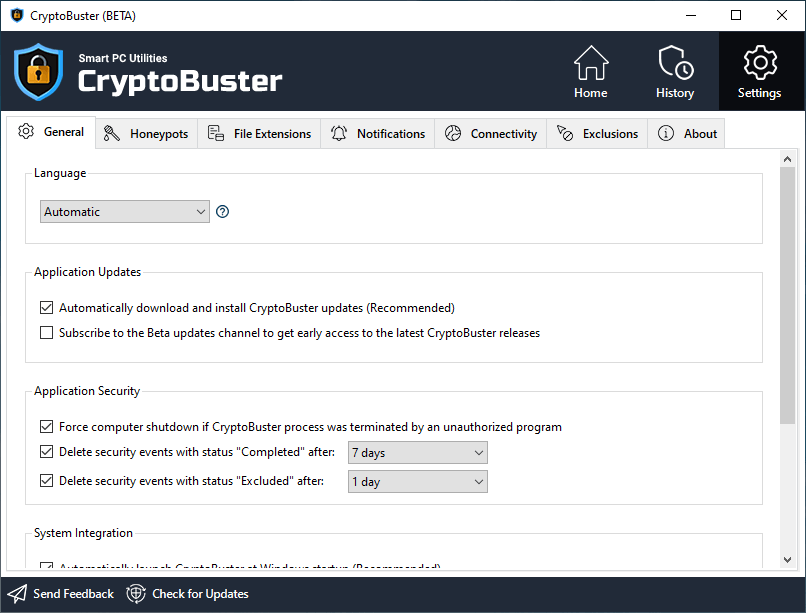
Language
Changes the user interface language, CryptoBuster will automatically restart to apply the new language settings.
Application Updates
Automatically download and install CryptoBuster updates
The CryptoBuster updater scheduled task will automatically download and install new CryptoBuster updates in the background.
Subscribe to the Beta updates channel to get early access to the latest CryptoBuster releases
This will allow CryptoBuster to download Beta updates; this will enable you to try new CryptoBuster features as soon as they become available.
Application Security
Force computer shutdown if CryptoBuster process was terminated by unauthorized program
Makes the CryptoBuster service process a critical system process; terminating the process will cause a BSOD. This option would help prevent ransomware from bypassing CryptoBuster by killing the CryptoBuster service process.
Delete security events with status "Completed" after
CryptoBuster will automatically delete completed security events older than specified days; this would help improve the management of security events and save disk space.
Delete security events with status "Excluded" after
CryptoBuster will automatically delete excluded security events older than specified days; this would help improve the management of security events and save disk space.
System Integration
Automatically launch CryptoBuster at Windows startup
Set the CryptoBuster service to start automatically on Windows startup; this will enable CryptoBuster to provide early protection against ransomware.
Scan the detected objects using the available AMSI compatible anti-malware engine
CryptoBuster will automatically scan detected programs using the AMSI compatible anti-virus software currently available on the system.
Feedback & Error Reporting
Enable the Debug Mode to help diagnose CryptoBuster issues.
CryptoBuster will create a log file in the CryptoBuster logs folder; the log file will contain all errors that occurred during CryptoBuster execution and would help us diagnose the software issues.
Automatically send error reports to Smart PC Utilities
CryptoBuster will automatically submit error reports to Smart PC Utilities via the feedback module.
Include additional technical and diagnostic information with the submitted feedback
CryptoBuster will include detailed technical information along with the submitted error reports and feedback (no personal data included); this information would help us provide better support.
Honeypots
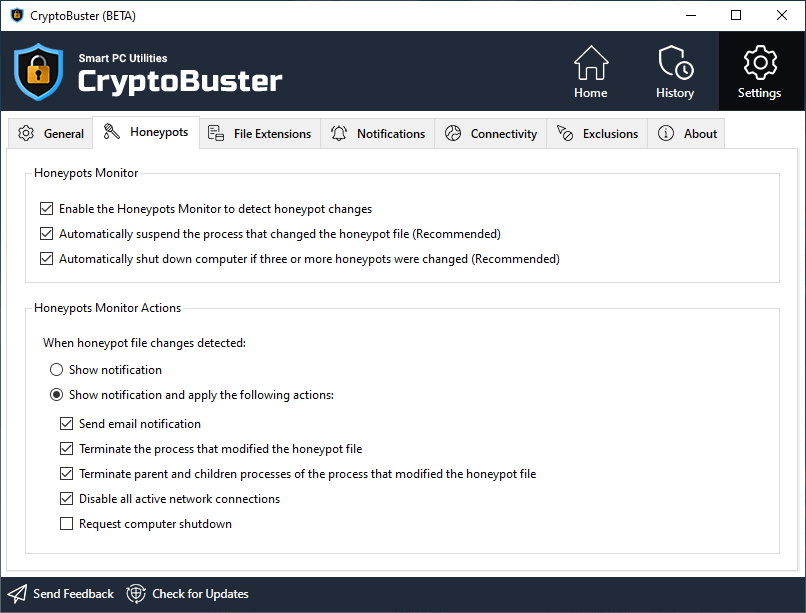
Honeypots Monitor
Enable the Honeypots Monitor to detect honeypot changes
Toggles the Honeypots Monitor on or off.
Automatically suspend the process that changed the honeypot file
CryptoBuster will automatically suspend the process that changed the honeypot file.
Automatically shut down computer if three or more honeypots were changed
If CryptoBuster detects that three or more honeypot files were modified by unauthorized programs, it will immediately terminate all running processes and forces the computer to shut down. This option would help protect your data from damage caused by an ongoing ransomware attack.
Honeypots Monitor Actions
Show notification
CryptoBuster will show a security alert and no actions will be applied.
Send email notification
CryptoBuster will send an email notification about the changed honeypot (you need to set up the email settings in the Connectivity tab so that CryptoBuster can send email notifications).
Terminate the process that modified the honeypot file
CryptoBuster will automatically terminate the process that changed the honeypot file.
Terminate parent and children processes of the process that modified the honeypot file
CryptoBuster will automatically terminate all parent and children processes of the process that changed the honeypot file.
Disable all active network connections
CryptoBuster will disable all active network adapters; this would help isolate the threat and prevent it from spreading to other computers on the network and may help prevent data exfiltration.
Request computer shutdown
CryptoBuster will show a computer shutdown count down as shutting down the computer can help prevent a further data damage.
File Extensions
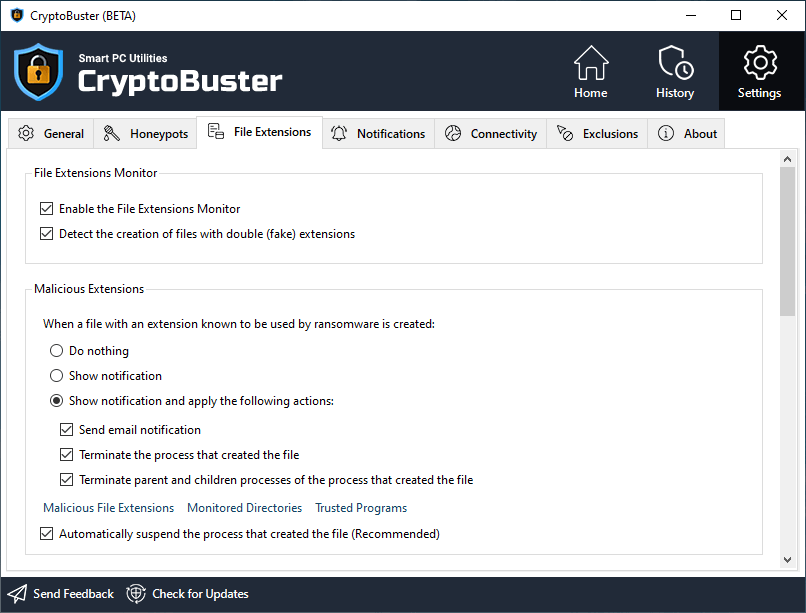
File Extensions Monitor
Enable the File Extensions Monitor
Toggles the File Extensions Monitor on or off.
Detect the creation of files with double (fake) extensions
Enables the File Extensions Monitor to detect files with a double (fake) extension; e.g., test.docx.exe
Malicious Extensions
Do nothing
Disables the Malicious Extensions Monitor.
Show notification
CryptoBuster will show a security alert when a file with a malicious extension is created; no actions will be applied.
Send email notification
CryptoBuster will send an email notification when a file with a malicious extension is created.
Terminate the process that created the file
CryptoBuster will automatically terminate the process that created the file with malicious extension.
Terminate parent and children processes of the process that created the file
CryptoBuster will automatically terminate all parent and children processes of the process that created the file with malicious extension.
Malicious File Extensions
Add or remove extensions from the malicious file extensions database.
Monitored Directories
Add or remove directories to be monitored by the Malicious Extensions Monitor.
Trusted Programs
Add or remove programs to be excluded from the Malicious Extensions Monitor.
Automatically suspend the process that created the file
CryptoBuster will automatically suspend the process that created the file with a malicious extension.
Potentially Dangerous Extensions
Do nothing
Disables the Potentially Dangerous Extensions Monitor.
Show notification
CryptoBuster will show a security alert when a file with a potentially dangerous extension is created; no actions will be applied.
Send email notification
CryptoBuster will send an email notification when a file with a potentially dangerous extension is created.
Terminate the process that created the file
CryptoBuster will automatically terminate the process that created the file with potentially dangerous extension.
Terminate parent and children processes of the process that created the file
CryptoBuster will automatically terminate all parent and children processes of the process that created the file with potentially dangerous extension.
Potentially Dangerous File Extensions
Add or remove extensions from the potentially dangerous file extensions database.
Excluded Directories
Add or remove directories to be excluded from the Potentially Dangerous Extensions Monitor.
Trusted Programs
Add or remove programs to be excluded from the Potentially Dangerous Extensions Monitor.
Automatically suspend the process that created the file
CryptoBuster will automatically suspend the process that created the file with a potentially dangerous extension.
Unknown Extensions
Do nothing
Disables the Unknown Extensions Monitor.
Show notification
CryptoBuster will show a security alert when a file of unknown type is created; no actions will be applied.
Send email notification
CryptoBuster will send an email notification when a file of unknown type is created.
Terminate the process that created the file
CryptoBuster will automatically terminate the process that created the file of unknown type.
Terminate parent and children processes of the process that created the file
CryptoBuster will automatically terminate all parent and children processes of the process that created the file of unknown type.
Trusted File Extensions
Add or remove extensions from the trusted file extensions database.
Monitored Directories
Add or remove directories to be monitored by the Unknown Extensions Monitor.
Trusted Programs
Add or remove programs to be excluded from the Unknown Extensions Monitor.
Trust extensions of registered file types
CryptoBuster will automatically trust files with extensions registered in the Windows Registry even if they are not added to the trusted file extensions list (disable this option to increase security as ransomware may register its file extension to bypass this protection).
Trust files created by foreground application processes
CryptoBuster will automatically trust files with unknown extensions created by processes that have a user interface (disable this option to increase security as ransomware process can create a user interface to bypass this protection).
Trust files created by processes signed with a valid digital signature
CryptoBuster will automatically trust files with unknown extensions that were created by processes that have their image files signed with a valid digital signature (disable this option to increase security as threat actors can sign the ransomware executable with a stolen digital signature to bypass this protection).
Automatically suspend the process that created the file
CryptoBuster will automatically suspend the process that created the file of unknown type.
Notifications
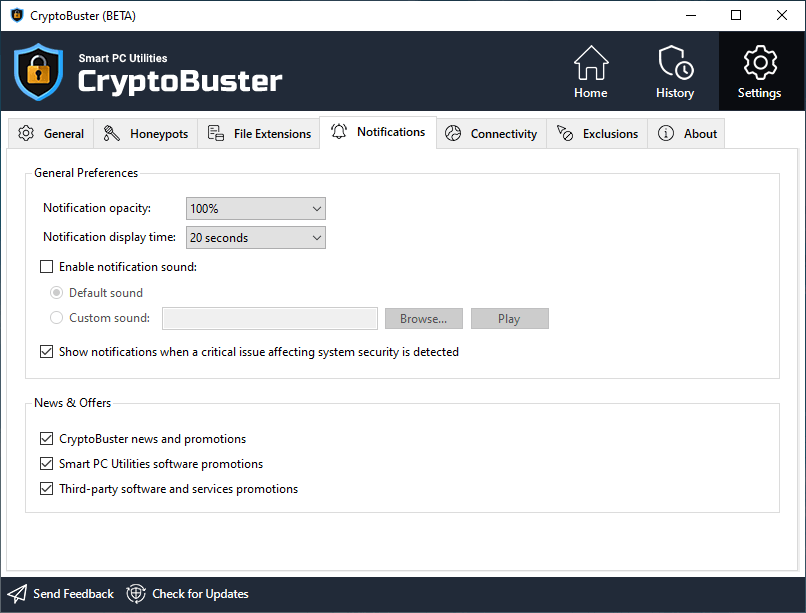
Show notifications when a critical issue affecting system security is detected
CryptoBuster will show security alerts when one or more of the CryptoBuster protection modules is disabled or not configured.
Connectivity
Proxy Server Settings
You can choose whether to use the default system proxy for CryptoBuster to connect to the Internet, or you can configure custom proxy settings.
Email Settings
Configure the email settings that CryptoBuster will use to send email notifications. Also, specify the email notification recipients.
Exclusions
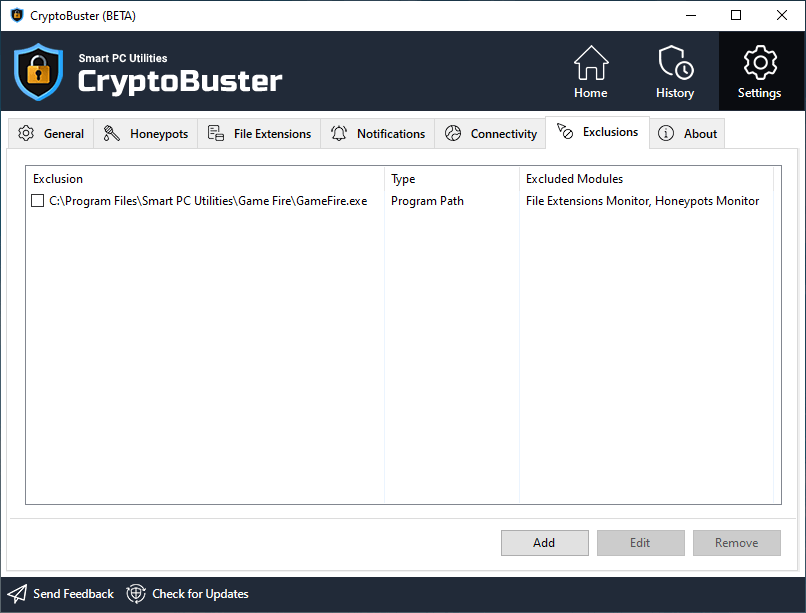
Use the Exclusions tab to manage CryptoBuster exclusions. Use exclusions to specify which programs, files, file extensions, and directories to bypass CryptoBuster protection modules.
Click the Add button to create a new CryptoBuster exclusion.
Click the Edit button to modify an existing CryptoBuster exclusion.
Click the Remove button to delete the selected CryptoBuster exclusions.