Honeypots
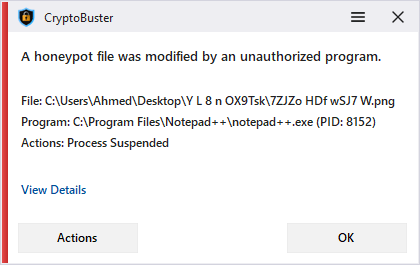
Honeypots are decoy files that CryptoBuster uses to detect malicious activities on your computer. This is an efficient and proven technique with low false-positive chances to detect and stop ransomware when they start to encrypt user files.
CryptoBuster can create hundreds of honeypots in strategic system locations with customized names and types that would allow honeypots to be targeted by ransomware before they start to encrypt the user's files. CryptoBuster closely monitors those honeypots and will automatically suspend and terminate any program that messes with them.
If CryptoBuster detects that a honeypot file was modified by a program that is not included in the CryptoBuster exclusions, it will apply the Honeypots Monitor automatic actions that include sending an email notification, suspending that program then terminating its process tree, and disabling all active network adapters (You can configure those actions in the CryptoBuster settings). CryptoBuster will also display a notification to the user informing him about the changed honeypot and the program that changed it; the notification dialog will contain links that you can use to get more details about this security event.
Before you can activate the Honeypots Monitor, you will need to create honeypot files to monitor for changes. You can either create honeypots manually customizing their names and locations or you can use the Honeypots Wizard to automate the creation and deployment of honeypots on your computer.
Create Honeypot Manually
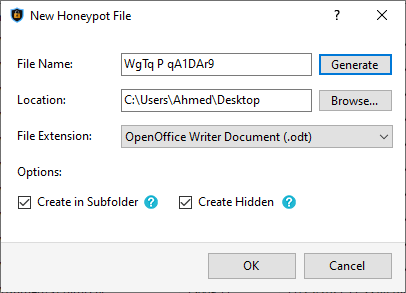
To create a custom honeypot file manually, follow the step below:
-
From the CryptoBuster dashboard, under the Honeypots section select Manage.
-
In the Honeypots Manager, click the Create File button located in the lower-right part of the CryptoBuster's user interface.
-
In the New Honeypot File dialog box, specify the honeypot file name, location, type, and options, then click the OK button to create and register the honeypot file with CryptoBuster.
|
|
CryptoBuster will immediately monitor the created honeypot file, so please do not modify the file to avoid undesired effects.
|
Honeypots Wizard
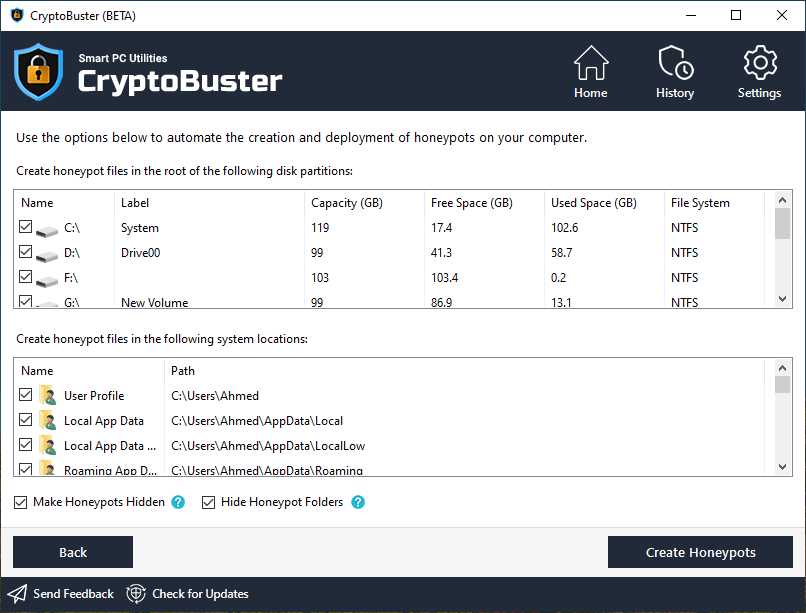
You can use the Honeypots Wizard to automate the creation of honeypots in every critical system location that is susceptible to ransomware attacks. CryptoBuster uses custom names and types that are optimized for each system location in order to maximize the effect of honeypots and allow them to be targeted by ransomware before they can reach the user's real files.
To create honeypots using the Honeypots Wizard, follow the step below:
-
From the CryptoBuster dashboard, under the Honeypots section select Manage.
-
In the Honeypots Manager, click the Honeypots Creation Wizard link located in the lower-left part of the CryptoBuster's user interface.
-
In the Honeypots Wizard, specify the locations where you want to create honeypots, then click the Create Honeypots button to create and register the new honeypots file with CryptoBuster.
|
|
It is very recommended to create honeypots in every system location to quickly detect ongoing ransomware attacks, thus protecting your data from damage.
|
|
|
The honeypots creation process may take some time, so please be patient.
|
|
|
Making honeypots hidden will improve the user experience and reduce the chance of accidentally changing those files; however, ransomware may bypass the created honeypots.
|
Honeypots Manager
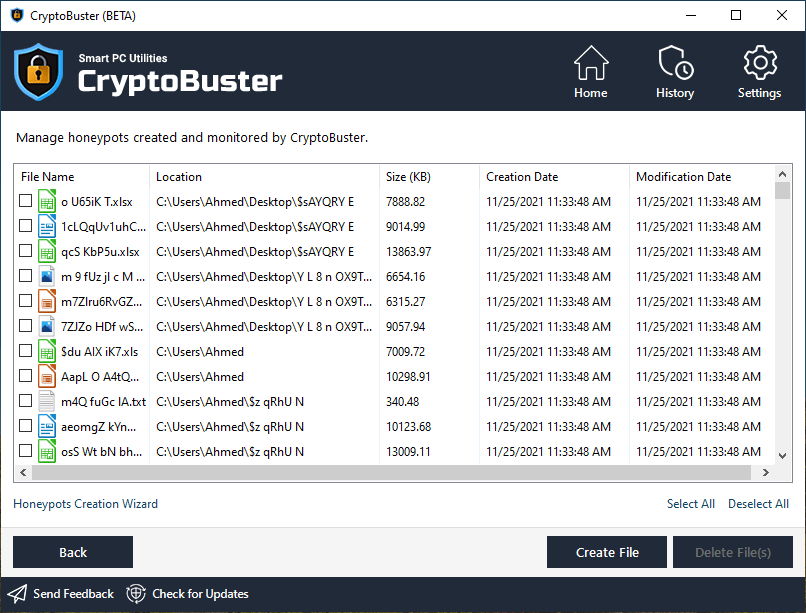
In the Honeypots Manager, you can browse and manage all honeypots registered with CryptoBuster and get their details like names, locations, and types.
To delete a honeypot file(s), select the honeypot you want to delete, then click the Delete File(s) button.
|
|
Use the Honeypots Manager to delete the created honeypots. DO NOT delete them directly or by using any other programs as CryptoBuster will flag this action as malicious and will suspend and terminate the process that deleted the honeypots and may force the computer to shut down unless you add this program to the CryptoBuster exclusions.
|